
In this short article I would like to share my knowledge about blackbox security testing of web applications. First of all, lets split blackbox security testing into two categories:
1) Passive analysis - actions, which simple internet user can do.
- DNS/whois/network
in this case we can find and analyze subdomains/subfolders.
E.g. use DNSmap, Dnsmap is a small C based tool that perform brute-forcing of domains. The tool can use an internal wordlist, or work with an external dictionary file.
Here is the screenshot how DNSmap looks like
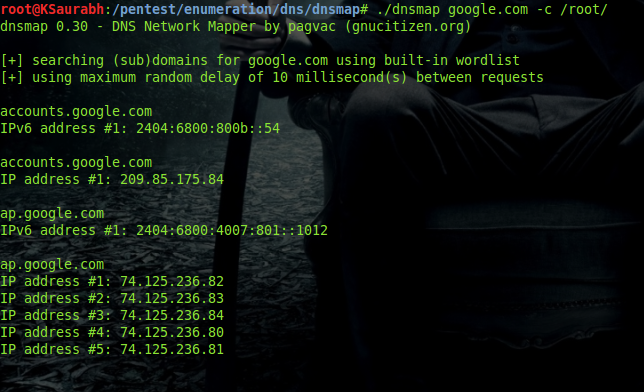
according to this screen, we get information about subdomains like accounts, ap and their IP's
- check component versions
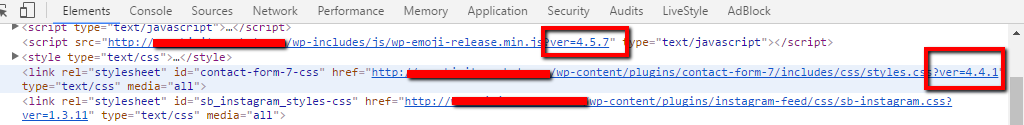
very often developers do not apply security updates for modules/core OR security patches on time. By analyzing the code we can find out versions of modules or core are used. For example look at this screenshot from a wordpress site, as we can see this site is using WP(v.4.5.7), plugin Contact Form(v.4.4.1), etc. What we need, is just find and learn security release notes for those plugins or core.
- check search engines
Search engines, like google, can help to find some security issues for web applications. For example:
site: example.com errorcan give us information on what program languages are used(e.g. PHP error) on the server and paths where those errors occur(/var/mysite/backend/myfunctionality/test.php), etc
- analyze code
just open the source of the page in firebug or analyze javascript/css and I am 100% sure you will find some interesting comments, very often we can find commented php code,etc. It may help you find issues with some functionality.
- analyze sitemap
in a sitemap we can find some private URLs, etc
- analyze robots.txt
very often developers want to hide important private folders from search engines but in this case they share them with the public.
2) Active analysis - some user actions which can be detected by a site owner(scanners - many connections, brute force, etc)
- portscan - we can use Nmap Network Scanning to find open ports and then, for example, try to connect to the mysql server with an empty or common password, etc
- file search - we can find some folders/files, for example using DirBuster, the multi threaded java application designed to brute force directories and file names on web/application servers. Or as an option use search engine with the query:
site:example.com Index Of- use other security tools like ZAP
